PUBLISHED: MARCH 7, 2022
On January 14th of 2022, the Security Service of Ukraine (SSU) stated that the country was the target of an ongoing “wave of hybrid warfare,” aiming to instill anxiety and undermine Ukrainian society’s confidence in the state’s ability to defend its citizens. The active cyber offensive by Russia against Ukraine began weeks before the Russian invasion on February 24. The hybrid cyber campaign included a combination of cyber intelligence, psychological warfare (PsyOps), distributed denial of service (DDoS), and multi-stage malware attacks targeting destruction of data and technology systems.

About the Author
Oleg Sinitsin
CEO & Founder of Dynamite Analytics
Oleg is a 20-year security software veteran leading Dynamite Analytics from its inception.
Cyberwarfare Chronology and Actors
The cyber campaigns executed against Ukraine in January-February of 2022 were prepared months in advance, including custom malware development, planting backdoor access, and bot farms (see Figure 1).
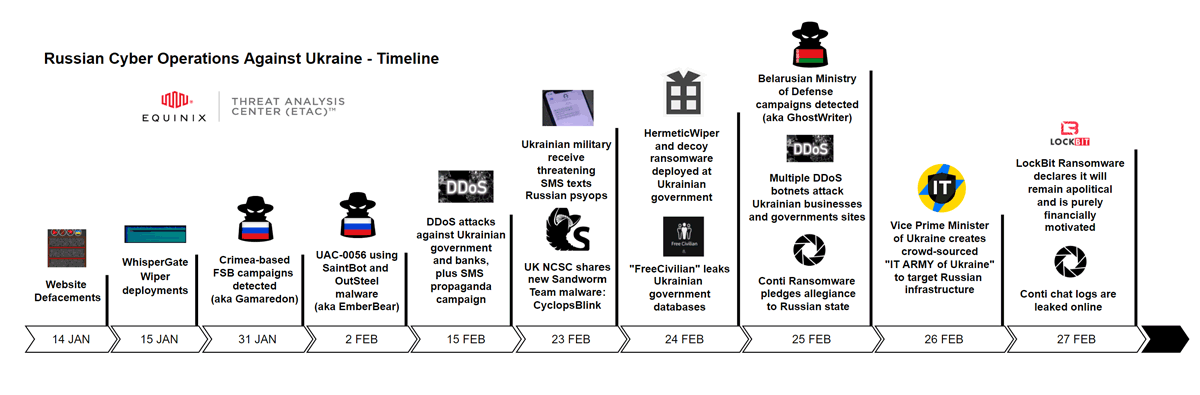
Figure 1: The Timeline of Russian Cyber Operations against Ukraine (Source: Curated Intelligence)
In the middle of January, multiple Ukrainian government websites were hacked and defaced to display a public warning that the visitors’ data was stolen and publicly shared online. At the same time, coordinated DDoS attacks were launched at over 70 websites, including the country’s energy, treasury, environment, veterans, and state emergency service departments. The Ukrainian SSU stated that during January they contained a total of 121 cyber-attacks against information systems and institutions. In early February, the SSU shut down two bot farms of 18,000 social network accounts that were spreading panic about bomb threats.
Starting January 13th, the first wave of data wiping attacks involving WhisperGate malware was unleashed on the Ukrainian government and banks. According to Microsoft, these cyber-attacks combined a destructive MBRLocker with the WhisperGate malware used to render the target computers unbootable and destroy data. Symantec found evidence of attackers gaining access to victims’ networks well in advance by exploiting Microsoft Exchange vulnerabilities as early as November 2021 and installing web shells before deploying the wiper malware.
On February 4th, Microsoft published research about the Gamaredon threat group (a.k.a. ACTINIUM) coordinated out of Crimea conducting spear-phishing attacks on Ukrainian entities and organizations. The apparent goal of this campaign was to perform exfiltration of sensitive information, maintaining backdoor access and moving laterally into related organizations. According to Symantec, the Gamaredon spear-phishing attacks were first seen in July of 2021, while the threat actor has been operating since 2013.
Starting in mid-February, leading to the day of the Russian invasion on February 24th, several Ukrainian government agencies, armed forces, and the large state-owned banks were hit with multiple DDoS attacks. The bank customers received threatening SMS text messages claiming that ATM machines were down.
On February 23rd, hours before the invasion, the two new strains of wiper malware called HermeticWiper and IsaacWiper were spotted by ESET. HermeticWiper followed the footsteps of WhisperGate wiper and ransomware decoys with the end goal of destroying data on targets’ devices and rendering them unbootable. According to Intel 471, these cyber-attacks have not been financially motivated as the destructive nature of wiper malware is not well suited for monetization.
Curated Intelligence created a map of threat actors involved in the Russia-Ukraine cyberwarfare on both sides, including nation-states and private hacktivist groups (see Figure 2).
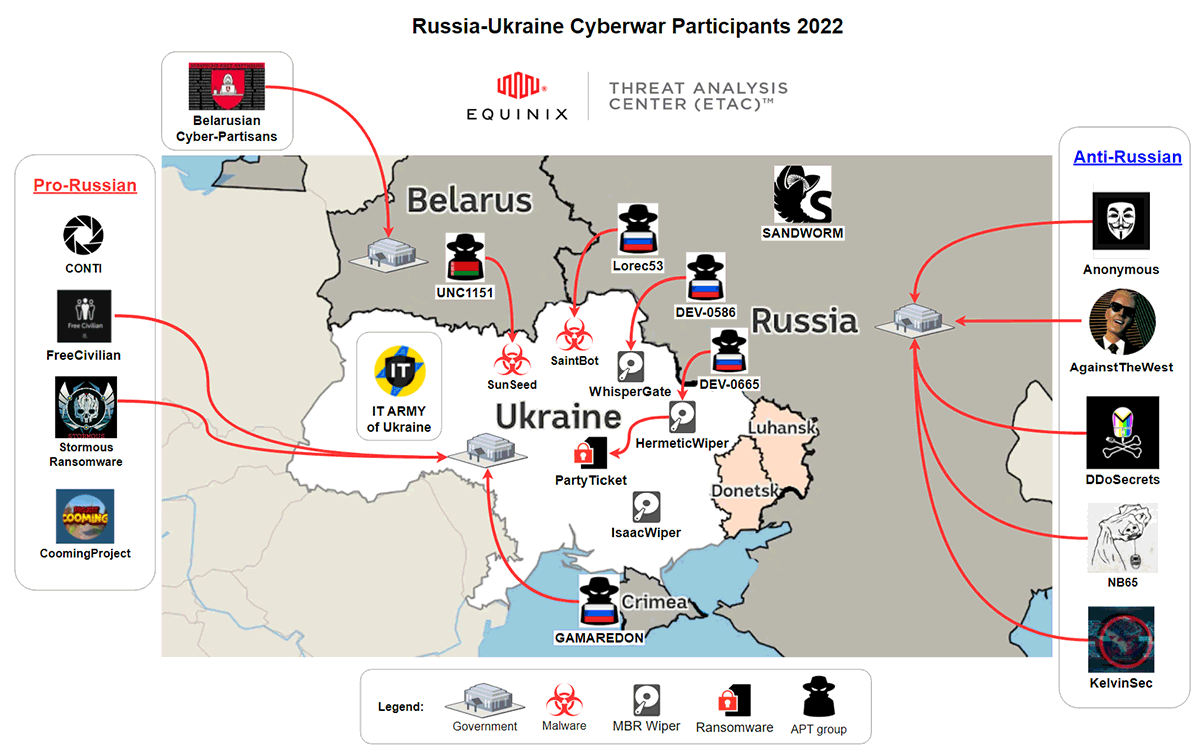
Figure 2: Russia-Ukraine Cyberwar Participants (Source: Curated Intelligence)
The Russian-speaking dark web forums have been quiet and steering away from political discussions. On February 26, The Ukrainian Ministry of Digital Transformation launched the “IT Army of Ukraine” inviting the international hacker community to fight a cyber war against Russia. Several pro-Ukrainian hactivists have taken jabs at the Russian government and private cyber gangs. Days after the Russian invasion, the prolific Conti ransomware group was exposed via a large data leak of their personal, financial, and technical records. The apparent objective of this data dump was to punish Conti for their expressed support of Russia. The levels of propaganda from PsyOps warfare on both sides have reached new heights, saturating social and traditional media with doctored evidence and unverifiable claims.
The Impact of Russian Cyberwarfare on Ukraine
As the signals of the imminent Russian aggression against Ukraine were mounting in January-February of 2022, many cybersecurity analysts were taking notice of the escalating cyber threats. The pessimistic predictions projected massive Ukrainian damages from the looming Russian cyber campaigns. Such expectations were founded on the recent Ukrainian history of major cyber incidents that were closely associated with Russia.
In 2015, Russia-linked threat actors took down a power grid, serving around 230,000 customers in western Ukraine. As discovered during the subsequent investigation, this cyber assault was planned for many months in advance, including custom malware development, patient reconnaissance, and deep infiltration.

As a result, the cyber-attack took down multiple power distribution centers with dozens of substations. The IT systems were damaged, and the backups disabled, leading to a long, painful process of recovery.
The cyber assaults against Ukraine continued in the following years. In 2016, the hackers took down the power in the part of Ukraine’s capital, Kyiv, with an enhanced, automated malware version of CrashOverride used in 2015. In 2017, another Russian attack featuring the malware “NotPetya” crippled the Ukrainian infrastructure, transportation, and financial institutions.
The 2022 Russian cyber offensive efforts against Ukraine surprisingly look far less effective than the previous highly disruptive cyber campaigns. It appears that recent cyber-attacks have been aimed at the organizations, companies and institutions directly tied to the Ukrainian government, while not heavily targeting the Ukrainian economy. Some analysts go as far to say that the Russian cyber capabilities appear to have been neglected over the last several years and lack prior sophistication.
Regardless of the underlying reasons, the Russian cyber offensive in Ukraine appears to play a marginal role in the current conventional warfare carried out with missiles and tanks. What is evident is that the information war has become the forefront of managing public opinion, and Russia is losing this war due to the harsh reality of their unjust occupation.
Other Thoughts
The Russian military plan appears to have been a swift military campaign with minimal Ukrainian resistance similar to the seamless annexation of Crimea in 2014, when very few shots were fired. Instead, the Ukrainian army has put up fierce fighting and has successfully stalled the inward penetration of the Russian forces. The longer the war goes on, the more Russian military grapples with supply chain issues, deflating army morale, and tactical vulnerabilities to the Ukrainian guerilla warfare. For now, President Putin remains defiant of the unilateral opposition of the Ukrainian population and the unprecedented barrage of international sanctions.
Russia and Ukraine have a common history, and yet the wounds of this war will likely haunt their future relationship for many years to come. Looking back, it did not have to be this way. Russia had an opportunity to be the loving brother to Ukraine by providing peaceful, meaningful support in economic and cultural spheres just like we saw between the West and East Germany. This opportunity has now been lost for the foreseeable future.
About Dynamite Analytics
Dynamite Analytics is a US-based SaaS company focused on network cybersecurity. The company’s leading platform, DynamiteLab, equips cyber and network operators with intuitive, machine-enabled analytics of network packet-captures (PCAPs). DynamiteLab operates as an international community hub for research and exchange of network traffic samples. Dynamite Analytics has won multiple US federal R&D awards pertaining to network traffic analysis.