Discover Your Network Like Never Before
Cloud-native network detection & response (NDR). The power of Zeek/Bro & Suricata in one package. Works with your SIEM/SOAR/ELK.
Network Detection & Response (NDR) is no longer optional:
- Equip your cyber operators with a deep understanding of your network environment.
- Make rapid, informed decisions based on the ground-truth of network traffic analysis.
- Quickly mitigate cyber threats based on comprehensive, actionable insights.
Better Understanding Leads to Better Decision Making
Enterprise security breaches continue to demonstrate a lack of network visibility and understanding of the operating environment, making it harder to reveal adversarial actions on the network even when those actions unfold over weeks or months.
Analysts struggle to identify relationships between multiple pieces of evidence and understand observed behaviors in context, greatly slowing down the decision-making process.
Dynamite Agent for AWS
- Best-in-class network traffic inspection is now available for your Cloud Security. Dynamite Agent combines Zeek/Bro and Suricata in a purpose-built NDR sensor for the cloud.
- We have made complex technology simple for deployment and integration with your Cloud SecOps process and tools.

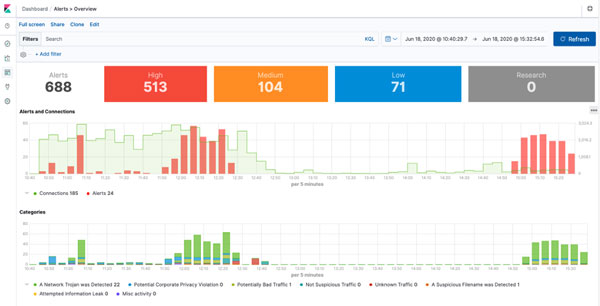
Dynamite provides answers to the critical cybersecurity and network management questions:
- What is happening on my network?
Network conversations, protocol insights, and behavior artifacts. - What is running on my network?
Asset fingerprints of PCs, BYOD, IT infrastructure, and IoT devices. - Where are threats and problems on my network?
Cyber threat detection and network troubleshooting.
Featured Article:
PCAP Analytics Redefined with PacketTotal
By Jamin Becker, CTO of Dynamite Analytics
Packet-capture (PCAP) files contain a complete copy of live network traffic and are essential for cybersecurity and network operations analysis. Unfortunately, PCAP datasets consume large amounts of storage, are technically complex and are notoriously difficult to data mine at scale. CISOs often overlook the packet-capture capability considering it a “nice-thing-to-have that we cannot afford.”
Featured Video:
Truths and Myths About Cybersecurity AI
By Oleg Sinitsin, CEO of Dynamite Analytics
After spending over 20 years in Cybersecurity, I am convinced that the most misunderstood industry term is Artificial Intelligence. At the end of the day, a security organization must be able to see through the vendor smokescreen and make intelligent purchasing decisions. In my recent video I discuss the use of AI in Cybersecurity, including general AI principles, Cyber AI systems, and network traffic analysis.
Dive below the surface to find what you’re missing.
Featured Webinar:
Packet Acquisition in the Cloud
By Adam Pumphrey, COO of Dynamite Analytics
NDR starts with traffic inspection by a network sensor, such as Dynamite Agent. Placement, deployment and configuration of network sensors can get complicated based on network type, size and architecture.
This webinar delivers an overview of common packet acquisition options with an emphasis on AWS cloud.