Does the world need another way to analyze network traces? We won’t convince everybody, but we think so.
We built DynamiteLab on a fresh approach for traffic analysis that empowers users of all knowledge levels to study and extract intelligence from network packet captures.

About the Author
Oleg Sinitsin
CEO & Founder of Dynamite Analytics
Oleg is a 20-year security software veteran leading Dynamite Analytics from its inception.

The Mystery of PCAP Analysis
Packet capture (PCAP) files contain a complete copy of live network traffic that has passed through a specific network location during a time window. They are similar in concept to short video clips recorded by a security camera.
When a motion detector triggers video recording, the resulting clip may contain useful evidence of a crime scene. Replaying video recordings is very simple with many kinds of software. The human mind is naturally trained to recognize and interpret visual scenes like those captured by a camera.
In fact, there is a tight community of network and cybersecurity professionals who comfortably dissect network packets and make sense of traffic patterns. For the rest of us, mere mortals, PCAP analysis remains largely a mystery.
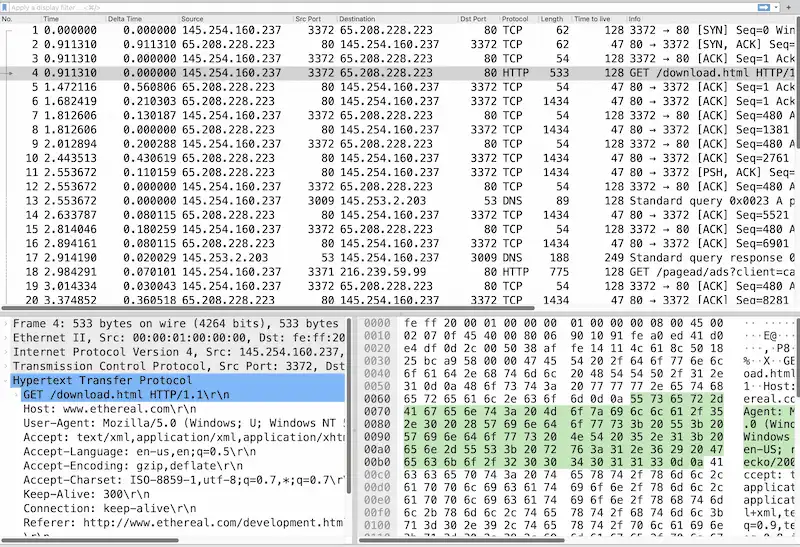
Each PCAP has a Story
Packet captures contain network connections between hosts interacting with each other via specific protocols, sending and receiving data. The complexity and volume of network communications are overwhelming to the human brain when presented line by line as connection records.
Instead, our mind craves information presented in a contextual way, by linking and associating data points with real-life meanings.
We created DynamiteLab based on the principles of effective learning, such as intuitive discovery and exploration of network communications. The platform is designed to tell a story of network behavior found in a given network traffic sample. We call it Packet Capture Intelligence.
DynamiteLab provides answers to the important questions of network and cyber operations:
- What is running on my network?- i.e., network assets.
- What is happening on my network? – i.e., network conversations and artifacts.
- What is interesting on my network? – i.e., cyber threats and network health.
Network Discovery & Exploration
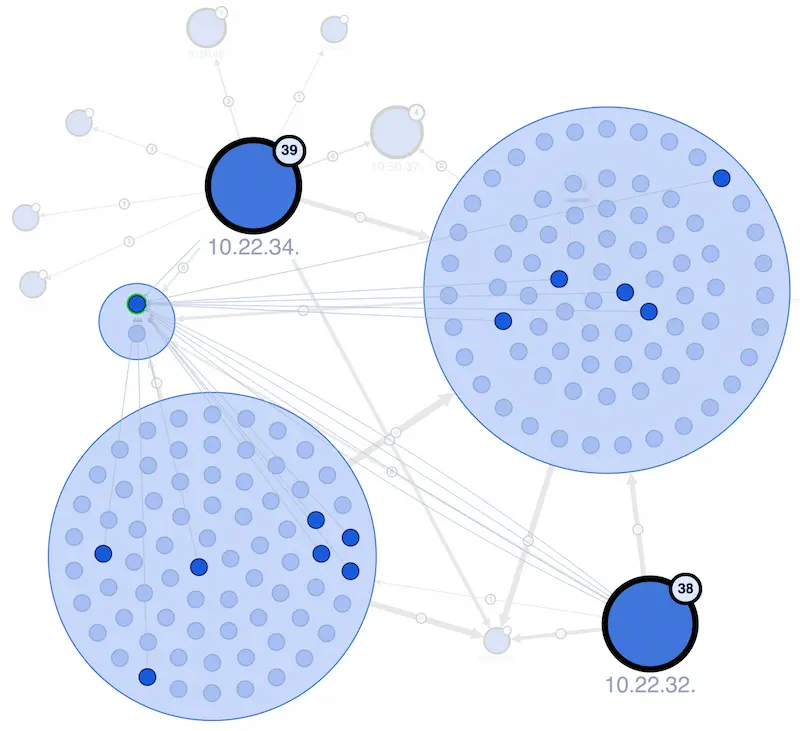
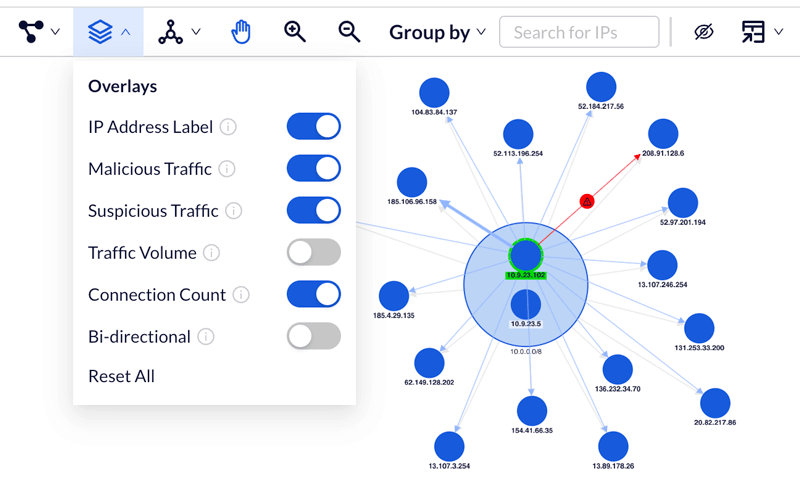
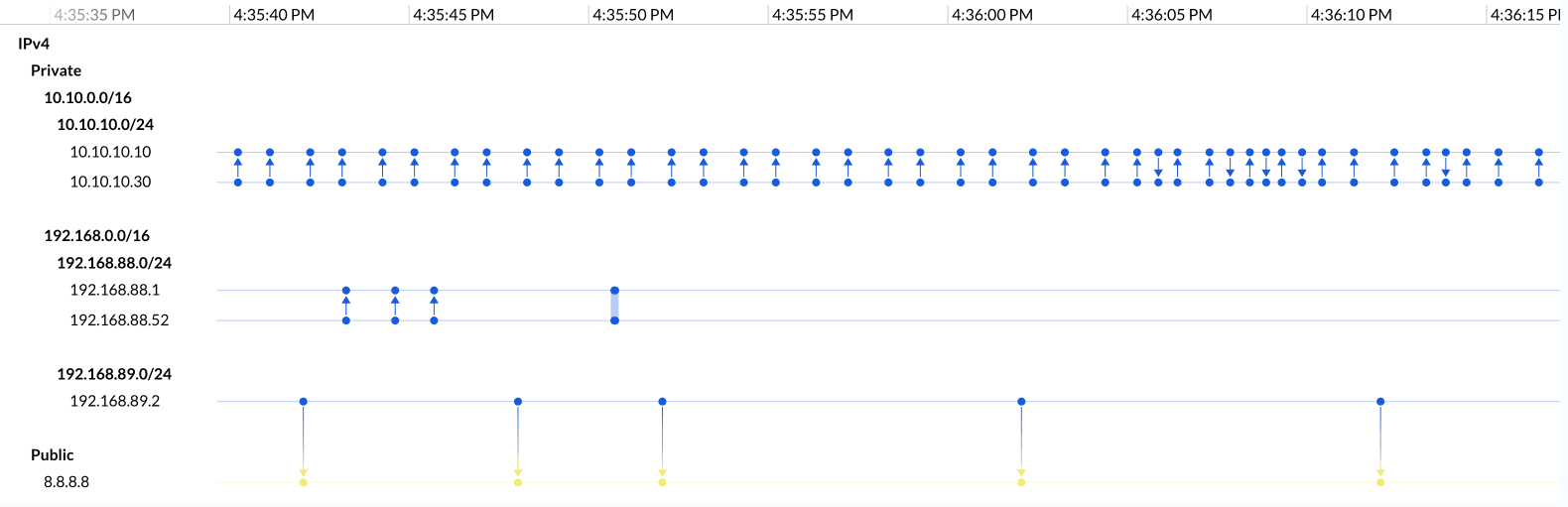
DynamiteLab facilitates network discovery via visual graph analysis. The Network Graph view starts the user on a journey of exploring host interactions and observing network behavior patterns.
The system supports multiple approaches of data navigation based on the use case. Interactive graph controls provide sophisticated clustering, positioning layouts, enrichment layers, filters, search and more.
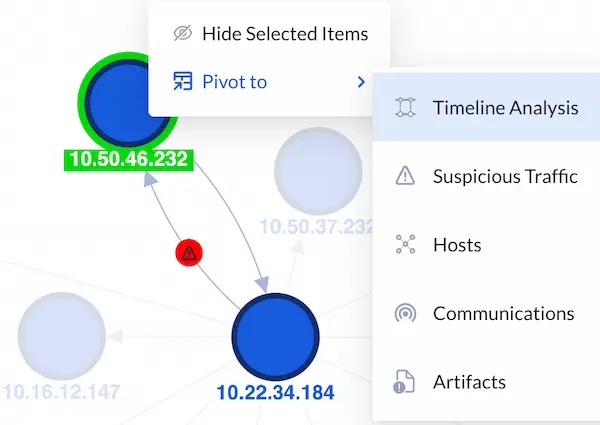
DynamiteLab delivers a self-guided analytic experience while helping users take the next step in the investigation using pivots.
For example, the network graph may highlight certain suspicious behavior and present pivoting options into the Timeline Analysis or the Communications view.
These network discovery features make DynamiteLab a great tool for threat hunting and generally learning the ins-and-outs of network environments.
More to Come
Our Community contains over 100,000 public PCAP samples, and it is completely free to use. Sign up today!
Please contact the Dynamite Analytics team if you would like to know more about the upcoming commercial release of DynamiteLab.
About Dynamite Analytics
Dynamite Analytics is a US-based SaaS company focused on network cybersecurity. The company’s leading platform, DynamiteLab, equips cyber and network operators with intuitive, machine-enabled analytics of network packet captures (PCAPs). DynamiteLab operates as an international community hub for research and exchange of network traffic samples. Dynamite Analytics has won multiple US federal R&D awards pertaining to network traffic analysis.