We just witnessed one of the most sophisticated cyber-attacks in history with the supply chain compromise of the SolarWinds software. This nation-state attack combined many unique adversarial techniques hidden under a trusted software update. In summary, this was a flawless campaign that successfully bypassed almost all information security controls. Every cybersecurity organization now faces a question – what to do next.

About the Author
Oleg Sinitsin
CEO & Founder of Dynamite Analytics
Oleg is a 20-year security software veteran leading Dynamite Analytics from its inception.
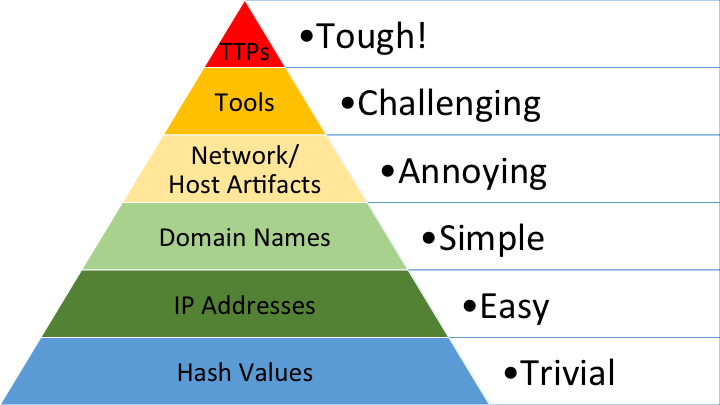
The Importance of the Pyramid of Pain
To better understand the complexity and impact of the SolarWinds incident, we have to consider the adversary’s motivation behind this attack. The vast majority of cyber-attacks are about the trade-off between the adversary’s effort vs. return on the investment. The “Pyramid of Pain” originally coined by David J. Bianco vividly demonstrates this principle – see Figure 1.
The Pyramid of Pain depicts a progression of indicators of compromise (IOCs) from the easiest at the bottom to the most difficult at the top. The progression of complexity and effort applies to both the attacker and the defender.
Figure 1: The Pyramid of Pain, David J. Bianco
While malicious payload hashes and compromised IP addresses are easy to detect, they are also the easiest to modify for the next attack. The changes to domain names involve slightly more hassle due to the registration process. The common defense mechanisms at this level are firewalls and signature-based IDS/IPS.
The tier of network/host artifacts and tools is where the adversarial level of effort starts going up significantly. The detection at this level forces attackers to make programmatic changes to their malicious software, methods of communication, and other behavioral artifacts. The effective defense strategy at this level often employs Endpoint Security, Network Detection and Response (NDR) as well as Security Orchestration, Automation and Response (SOAR).
Tactics, Techniques and Procedures (TTPs) are at the top of the Pyramid. They describe adversarial strategies, actions and methods across all stages of an attack. For more information see MITRE ATT&CK. Defender’s understanding of TTPs exposes the mind of an attacker and is the most effective deterrent in terms of the adversary’s time and effort invested into an attack. At this level of maturity, the cyber defense mindset switches from thinking reactively, to thinking proactively. This places the emphasis on having an in-depth understanding of your own environment, threat intelligence on your potential adversaries and leveraging tools and techniques like threat hunting playbooks and machine-learning.
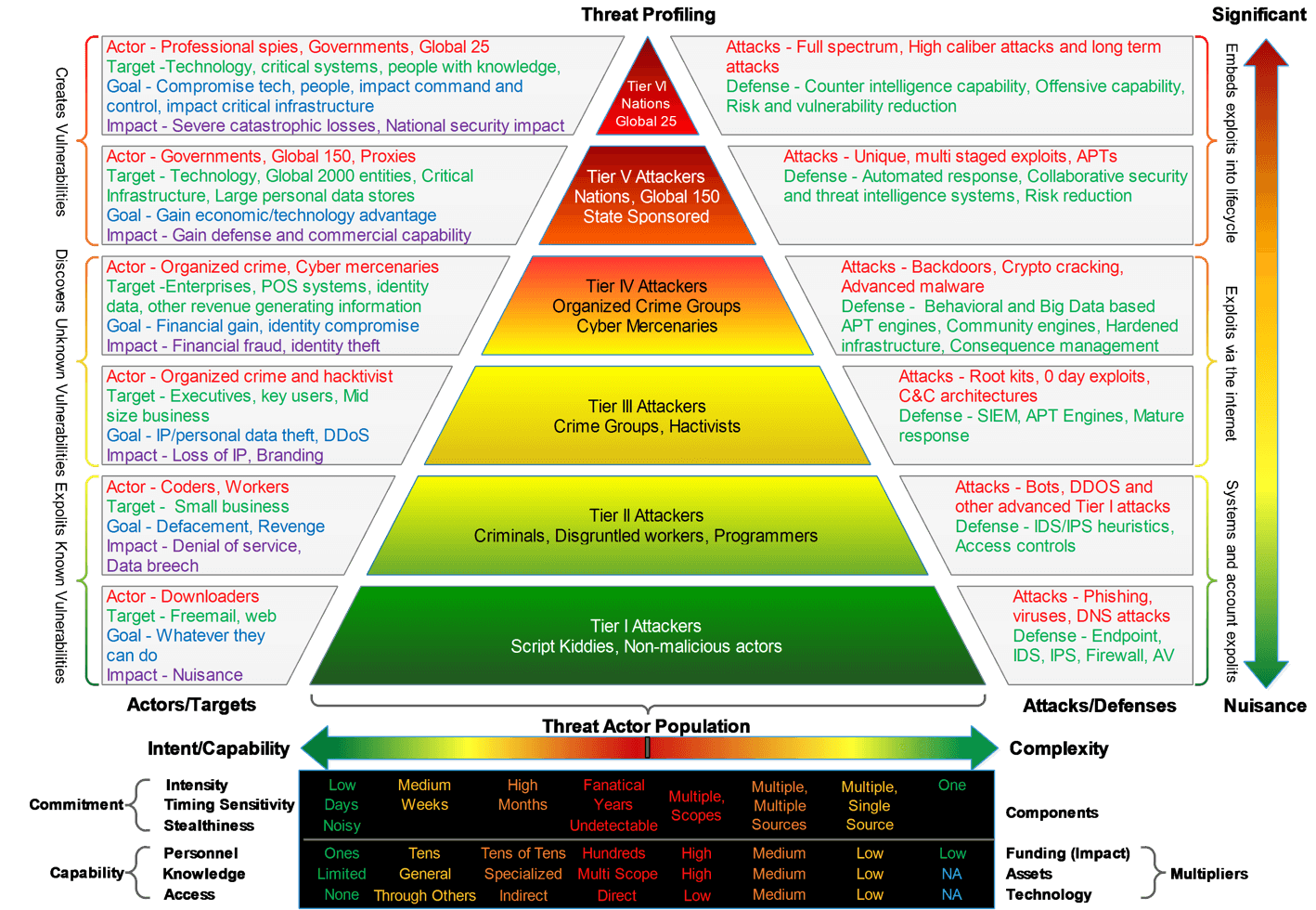
Greg Reith, while working on T-Mobile’s Threat Management team, greatly expanded upon the Pyramid of Pain from the perspective of a global telecom provider – see Figure 2.
Figure 2: Prioritizing Cyber Threats With Real-Time Threat Intelligence, Greg Reith
At the very top, there are nation-state actors with nearly unlimited resources who are in the position to craft custom techniques for the preselected top-reward targets. The SolarWinds supply chain attack falls into this category. Obviously, the most terrifying aspect of this attack was the trusted malicious update in the Orion software. The Orion platform is designed for managing and monitoring network infrastructure. By installing a trusted, digitally signed update, all unsuspecting Orion users were immediately at a tremendous risk across their network environments.
Why is SolarWinds so Hard?
What is not getting enough attention is the sophistication of the SolarWinds attack that took place after the malware Delivery stage. After the trojan DLL plugin had been installed, it opened a door for the attack to be carried out. The subsequent steps were carefully crafted with much ingenuity. As pointed out by John Hubbard of SANS Institute, each stage of the attack featured skillful, unique TTPs that were very difficult to detect – see Figure 3.

Figure 3: SolarWinds Blue Team Perspective and Opportunities, John Hubbard
The SolarWinds attack preparation required years of research and development by a state-sponsored actor. The exact TTPs have now been well researched and integrated as known IOCs in various cybersecurity solutions. From now on, threat actors will not be able to simply replay the old attack. What is likely to happen next is development of SolarWinds variants based on the “food chain” in the Pyramid of Pain.
The “success” of the SolarWinds attack has taught threat actors to put more effort in preparation and to be more patient during discovery. This has proven to be an effective way of getting to higher value assets. Subtle behavior patterns are likely to emerge on a broader scale among the subsequent copy-cat campaigns, and digitally signed software updates will remain a big target. Attacks of this nature require the highest R&D investment and are limited to very well-funded nation-state and crime groups.
The less sophisticated threat actors will be making smaller modifications. They have plenty of opportunities for altering the original tools and methods to bypass the obvious SolarWind IOCs, such as domains, files, registry keys, etc. The crime groups in the middle of the Pyramid, as shown on Figure 2, are the most likely actors to pursue data exfiltration for commercial purposes, such as credit card data, customer information, intellectual property from a variety of enterprise targets.
What to Do Next?
Detecting malware inside the vendor software updates may be an ambitious undertaking for most cybersecurity organizations. This issue must be addressed at the vendor management level, and yet it will still carry the risk of the unknown. Keeping that in mind, there are a few practical steps that cyber defenders can take for improving their detections and forcing the attackers to move on and look for easier prey.
- Making sure you don’t have a compromised SolarWinds system – This is a starting point that includes the inventory of your existing software and deployment of signature-based host/network IDS tools that cover all latest SolarWinds IOCs.
- Detection of behavior patterns and artifacts similar to the SolarWinds attack – The full analytic kill-chain coverage is achieved via Endpoint Security, NDR and SOAR solutions. The SolarWinds specific detections include: domain name analysis, unusual traffic sources, suspicious Windows executables, commands and processes, etc.
- Proactive knowledge gathering about your environment and potential adversaries – This is a shift from a reactive to proactive security operation. A threat hunting program coupled with threat intelligence analysis is a must.
- Machine learning (ML) techniques – Building behavior baselines of network assets can be effective in detection of suspicious outliers and zero-day threats. Make sure you understand the vendor claims regarding their ML capabilities. The more transparency, the better.
Additional Resources About the SolarWinds Attack
- FireEye Threat Research, “Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor”
- Microsoft 365 Defender Research Team, “Deep dive into the Solorigate second-stage activation: From SUNBURST to TEARDROP and Raindrop”
- Palo Alto Unit42, “SolarStorm Supply Chain Attack Timeline”
- CISCO Talos, “Threat Advisory: SolarWinds supply chain attack”
About Dynamite Analytics
Dynamite Analytics is a US-based SaaS company focused on network cybersecurity. The company’s leading platform, DynamiteLab, equips cyber and network operators with intuitive, machine-enabled analytics of network packet-captures (PCAPs). DynamiteLab operates as an international community hub for research and exchange of network traffic samples. Dynamite Analytics has won multiple US federal R&D awards pertaining to network traffic analysis.