The Colonial Pipeline cyber-attack, leaving the US East Coast with a fuel-supply shortage, has been a somber reminder of the broad-scale impact caused by ransomware. Many organizations come to a terrifying admission that sooner or later they may be breached, and they will not catch the intrusion on time. Dwell time is becoming a buzzword in the age of ransomware, referring to the amount of time an attacker remains undetected inside the network. It is a key indicator whether an organization can stop an attack before the damage is done.

About the Author
Oleg Sinitsin
CEO & Founder of Dynamite Analytics
Oleg is a 20-year security software veteran leading Dynamite Analytics from its inception.
Big Business of Ransomware-as-a-Service
Ransomware is becoming the most lucrative cyber-crime model, and it now exceeds financial rewards of point-of-sale malware, such as the theft of payment transaction data. Ransomware is a crime of extortion that paralyzes the victim’s business by encrypting its data. It is now often combined with data theft and a threat of public disclosure. A victim is presented with a choice to pay for the restoration of business operations or suffer severe consequences.
The ransomware crime industry has now adopted the Ransomware as a Service (RaaS) business model. A RaaS development company, such as DARKSIDE used in the Colonial Pipeline incident, runs a revenue-sharing, subscription-based model for its affiliates who execute attacks.
The level of criminal sophistication now mirrors the enterprise software industry with customer support, documentation and software updates. For example, DARKSIDE affiliates go through the interview process and hands-on training of the RaaS control panel, including ransomware configurations, victim management, etc.

Advanced RaaS variants like DARKSIDE are clearly reaping financial benefits through high payouts. Colonial Pipeline reportedly paid a $4.4M ransom in bitcoin to avoid tens of million dollar losses and, according to the company’s CEO, “it was the right thing to do for the country.” While paying ransoms is widely frowned upon by businesses and the government agencies, payouts continue to be an ongoing trend bringing more and more dollars to the ransomware industry.
Assume You Will Be Hacked and Get Ready for Post-Exploitation
Before launching ransomware attacks, criminals often evaluate the financial state of their targets. This means if your organization is known to have financial resources, it very well may be on the hit list. Once reconnaissance and RaaS preparation are complete, attackers have an array of options to establish initial access. A mature organization may be on top of all of its security controls and yet still suffer from attack vectors like zero-day exploits and supply chain compromises. The bottom line, you have to assume that you will be hacked.
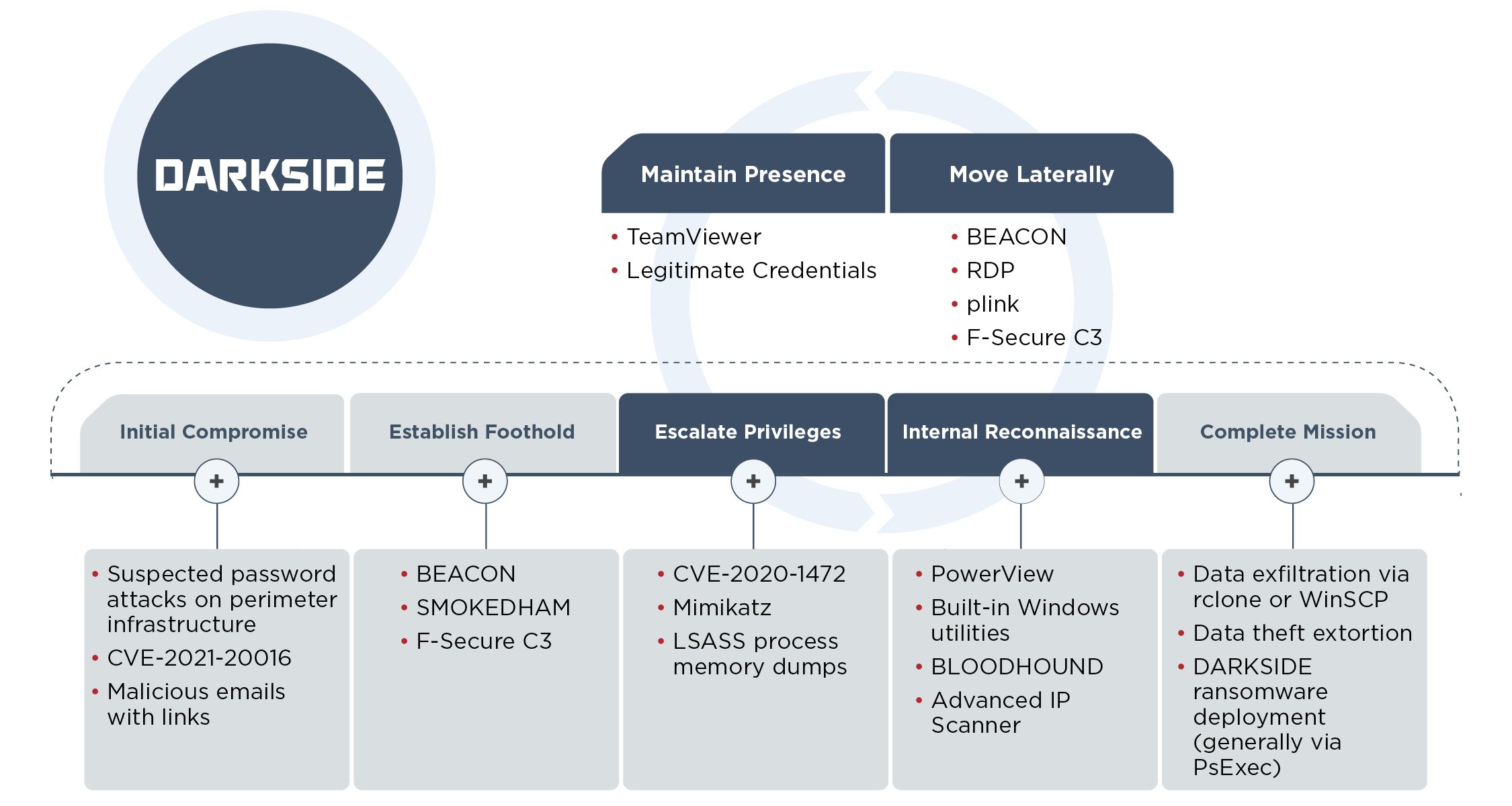
Once the adversary has gained a foothold in your environment, the dwell time clock has started. A ransomware attacker has to perform a series of tactics (see MITRE ATT&CK) before reaching the final step of Impact, when a victim’s data is encrypted. Each step in the attack sequence takes time and leaves a trace. According to FireEye Threat Research, DARKSIDE affiliate threat actors use a common combination of tactics, techniques and procedures (TTPs) during the post-exploitation phase (see Figure 1).
Figure 1: DARKSIDE Ransomware Attack Lifecycle and Common TTPs (source: FireEye)
The Window of Dwell-Time
According to FireEye, the majority of ransomware attacks take at least 3 days before inflicting damage, while approximately half of the attacks deploy ransomware in less than 50 days after initial compromise.
As a comparison, the median dwell time for an organization to detect an intrusion is 24 days as indicated in 2021 M-Trends Report with median internal team’s detections of 12 days and external detections of 73 days. However, the median dwell time of ransomware intrusions is only 5 days, giving hope that in-progress ransomware campaigns can be successfully stopped.
The dwell time analysis highlights several ransomware mitigation strategies:
- Zero-Trust Model – Moving from the traditional perimeter security approach to the zero-trust model is no longer optional. Zero Trust assumes no implicit trust granted to assets or user accounts based on their physical or network location and instead requires continuous, granular verification of the operational picture in real-time. Ultimately, zero-trust creates more hurdles for attackers, buys more detection time and creates more opportunities for an intruder’s exposure.
- Internal vs. External SecOps – Building your internal team’s capabilities is paramount in detecting sophisticated threats. A dedicated threat hunting process will move the SecOps mindset from reactive to proactive and will lead to better and faster decisions. Trusting a qualified 3rd party provider may be necessary, but it often results in longer dwell time.
- Planning for Ransomware Incidents – Organizations that implement ransomware specific countermeasures are much better positioned to sustain their business operations in case of an attack. Ransomware detection and investigation processes should be coupled with business continuity planning, such as effective backup procedures and critical systems isolation. Working through a hypothetical attack scenario and its potential impact can be a life saver when disaster strikes.
About Dynamite Analytics
Dynamite Analytics is a US-based SaaS company focused on network cybersecurity. The company’s leading platform, DynamiteLab, equips cyber and network operators with intuitive, machine-enabled analytics of network packet-captures (PCAPs). DynamiteLab operates as an international community hub for research and exchange of network traffic samples. Dynamite Analytics has won multiple US federal R&D awards pertaining to network traffic analysis.