Why should your team be leveraging network metadata for more mature cybersecurity?
Many cybersecurity vendors use the term network metadata without clearly defining what it is. Generally speaking, metadata is descriptive information about the data, or “data about the data.” Network metadata carries individual traits pertaining to the structure of network protocols and packets. Specifically, it represents telemetry of network connections and the artifacts associated with these connections.
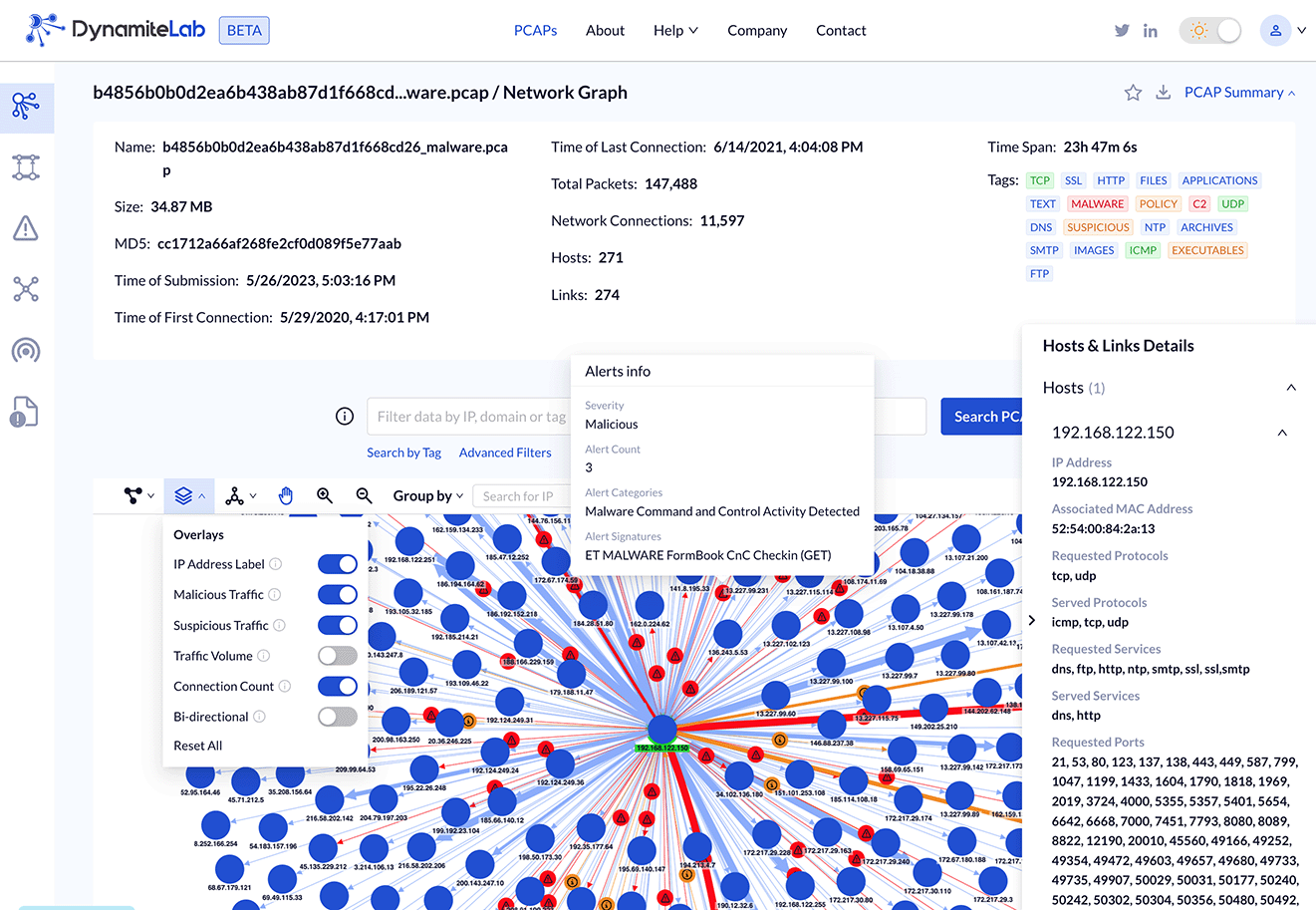
Examples of Network Metadata from a PCAP in DynamiteLab
Metadata acquisition technologies are generally categorized as Deep Packet Inspection (DPI) or network traffic inspection with many notable differences. Flow data (e.g. NetFlow, IPFIX, sFlow, etc.) is a commonly used set of the OSI Layer 2-4 telemetry, such as source, destination, protocol, bytes sent/received. Various flavors of flow data are produced by network infrastructure devices, and they offer a good start in understanding the basic trends of network traffic. Unfortunately, flow data is not always enough for advanced cyber threat detection within the application-layer context.
As opposed to flow data, network packet capture files (PCAPs) contain the full detail of network traffic. PCAPs are the most detailed historical record of what happened on the network, but they come with high storage and data processing requirements. The middle ground is found in traffic inspection technologies that can be customized to extract meaningful Layer 3-7 metadata with an emphasis on Layer 7 application communications. One distinct advantage of this approach is that this metadata can be used effectively for behavior cyber threat detection, while only taking a fraction of the full PCAP volume.
Dynamite’s PCAP analytic platform, DynamiteLab, leverages several network traffic inspection technologies, including Zeek, Suricata and some proprietary network analyzers. For example, Zeek metadata consists of 50+ logs with comprehensive connection records and application-layer transcripts. This information is naturally structured as time-series events corresponding to network conversations, such as: TCP/UDP/ICMP connections, HTTP requests and replies, DHCP leases, SNMP messages, SSH connections, and much more. Zeek metadata is combined with Suricata’s network intrusion detection capabilities and is enriched with additional indicators.
In summary, network metadata delivers a mechanism to describe network traffic behavior. It is essential for cyber threat hunting, digital forensics, and network performance analysis. For more information, see our article about Packet Capture Intelligence.
About Dynamite Analytics
Dynamite Analytics is a US-based SaaS company focused on network cybersecurity. The company’s leading platform, DynamiteLab, equips cyber and network operators with intuitive, machine-enabled analytics of network packet-captures (PCAPs). DynamiteLab operates as an international community hub for research and exchange of network traffic samples. Dynamite Analytics has won multiple US federal R&D awards pertaining to network traffic analysis.