In today’s world of increasingly complex cyberwarfare, Security Operations Centers (SOCs) have to contend with an overload of cybersecurity indicators and their supporting information. Incident responders must make critical decisions with limited evidence and little time. Cyber Threat Intelligence and Threat Hunting are designed to augment the SOC process constraints with advanced levels of situational awareness and decision support.

About the Author
Oleg Sinitsin
CEO & Founder of Dynamite Analytics
Oleg is a 20-year security software veteran leading Dynamite Analytics from its inception.
Observation and Orientation
“For one offensive (e.g., malware) line of code (LOC), on average defenders write 100,000 LOCs” is a statement coined by the famed security expert “Mudge” Peiter Zatko. Defenders perform exponentially more work and have substantially higher resource costs than their adversaries.
Security organizations face high complexity of attacks coupled with ongoing changes of a threat landscape. One approach to this challenge comes from conventional warfare and consists of systematic learning of adversarial intentions, capabilities, and actions within a given environment.
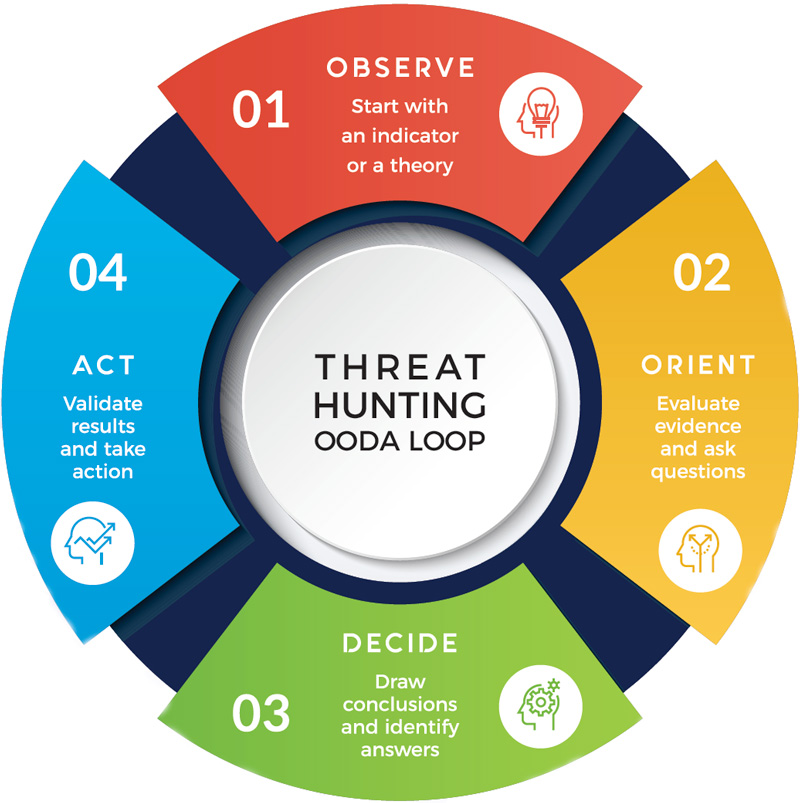
The OODA loop (Observe-Orient-Decide-Act) was developed by US Air Force Colonel John Boyd, and it has been adopted by many military and business organizations around the world. The OODA loop frames the method of agile decision-making in conditions of uncertainty commonly found in cyberwarfare.
Cyber Threat Intelligence (CTI)
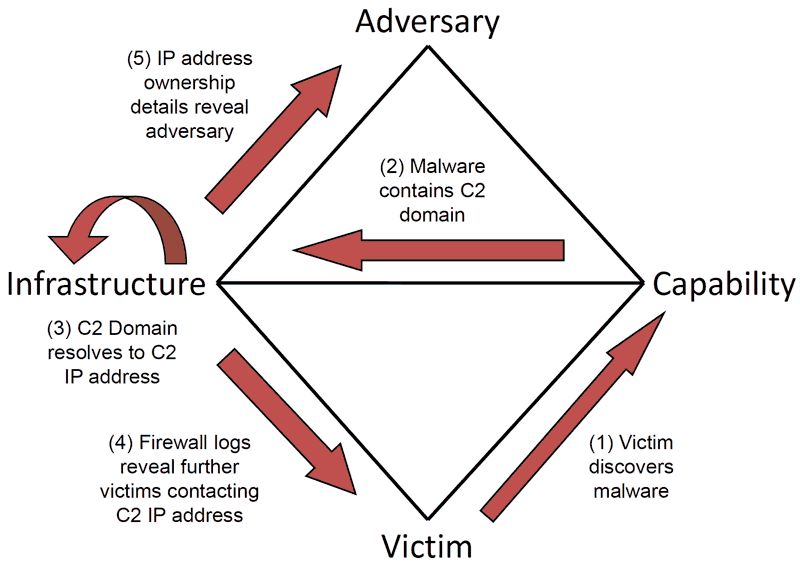
In 2013, a group of cybersecurity researchers published a white paper titled the Diamond Model for Intrusion Analysis, which aligned with the OODA principles of observation and orientation. The Diamond Model is a threat intelligence framework, describing an Adversary, the Capability to do harm, the underlying technology Infrastructure, and the targeted Victim. The model emphasizes evaluation of the attacker identity (e.g., APT group attribution) and the attacker’s behavior expressed via the steps in a kill-chain (e.g., MITRE ATT&CK). It can be further extended to focus on the capability match-up between the attacker and the defender.
Figure 2: The Diamond Model
- Adversary – types and identities of present and potential attackers
- Capability – tools, methods, and processes of both attackers and defenders to match up against each other
- Infrastructure – the state of control by both attackers and defenders over the defender’s environment
- Victim/Defender – business entity, its assets, vital data, and critical processes that can be targeted by an attack.
While the Diamond Model facilitates discovery of malicious actors and activities, it lacks flexibility to describe all elements of the Cyber Threat Intelligence (CTI) domain.
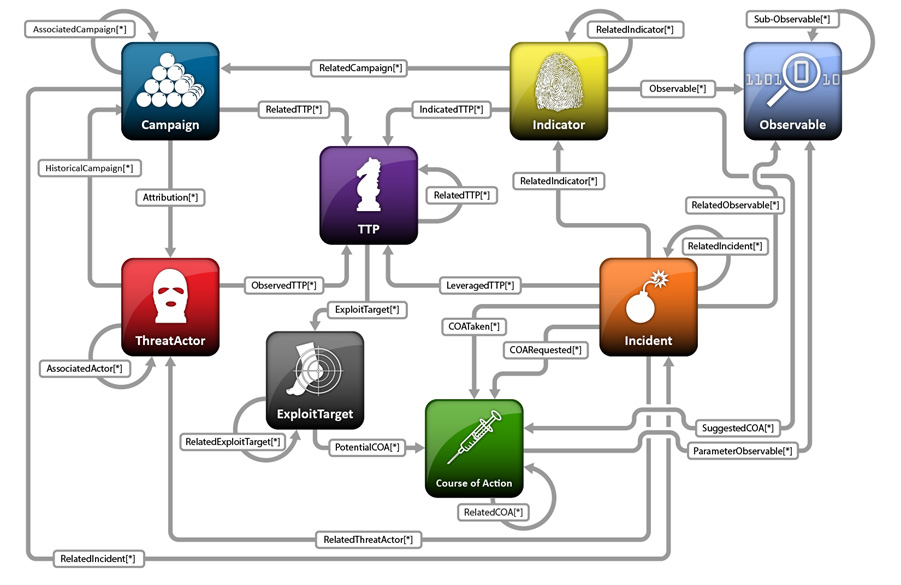
In 2014, the MITRE corporation produced a specification of the Structured Threat Information Expression (STIX) as a language for describing, exchanging, and analyzing cyber threat information.
STIX alongside several other efforts created a rich mechanism of building generic CTI models. STIX categorizes and connects CTI via Objects and their Relationships and sets the foundation for contextual analysis. STIX has now been widely adopted by the cybersecurity industry.
Figure 3: STIX Objects and Relationships
Threat Hunting
Threat hunting (TH) can be defined as a human-driven, machine-enabled process of proactively searching for cyber threats before harm is done. Instead of CTI’s emphasis on the adversary, TH focuses on what is happening in the defender’s environment. The combination of CTI + TH exposes the mind of an attacker in the form of tactics, techniques, and procedures (TTPs) and serves as a great deterrent from sophisticated and highly damaging cyber threats.
The key TH objective is to discover unfolding cybersecurity attacks early in the kill-chain and to understand the nature of an incident before an adversary can inflict damage. Key TH process metrics include Dwell Time (i.e., time from infection to detection) and the Rate of Reinfection (i.e., frequency of repeated compromises).
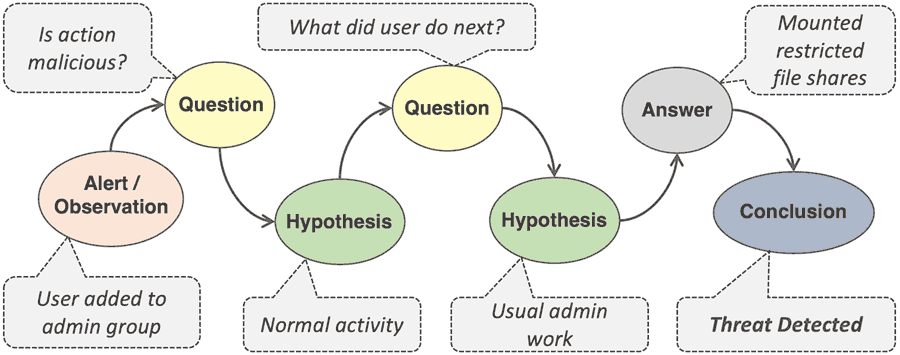
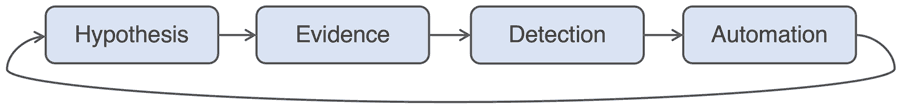
A typical threat hunt is an exercise that involves mining, linking, and analyzing cybersecurity information. It follows the sequence of investigation steps from question to hypothesis and ultimately to a conclusion. Hypothesis starts with a human observation or a human/machine-generated alert. Observation originates in internal knowledge of the environment and external intelligence.
Figure 4: Threat Hunting – Observation to Conclusion
The key to a valid hypothesis is to know what questions to ask. The process further involves contextual analysis of the evidence, correlation with indicators of compromise (IOCs), and the use of machine analytics. Evidence consists of the data relevant to an investigation, including network metadata and artifacts, endpoint detections, and CTI sources. Automated data enrichment and pivoting between data points add much efficiency to the TH process. Statistical and machine-learning (ML) techniques can also highlight anomalies and help validate assumptions.
Figure 5: Threat Hunting Loop
In summary, TH enables cyber analysts to gain thorough understanding of their own environment and, coupled with CTI, raises awareness about potential adversarial actions. It is a human-driven process of agile decision-making that raises resiliency against sophisticated cyber-attacks and is an effective training ground for cybersecurity personnel.
About Dynamite Analytics
Dynamite Analytics is a US-based SaaS company focused on network cybersecurity. The company’s leading platform, DynamiteLab, equips cyber and network operators with intuitive, machine-enabled analytics of network packet-captures (PCAPs). DynamiteLab operates as an international community hub for research and exchange of network traffic samples. Dynamite Analytics has won multiple US federal R&D awards pertaining to network traffic analysis.